In this article, we explore some key tips and best practices to bolster Mac security. While I was writing this post Apple timely did release this ad:
It is only 8 minutes, watch it if you have time. It is fun but also serious.
Lets review the basic Apple security features shown in the video above
This Apple ad does a great job of illustrating how your Mac is protected in simple language that can be understood by everyone. Let's review them quickly:
Biometrics
Touch ID made its laptop debut in the MacBook Pro in 2016, it integrated on the right side of the Touch Bar. This is not only great for device security but allows to migrate to a more secure world, enabling us to use passkeys instead of passwords. See below for more about this topic under passkeys.
Find My:
Once you are logged in on your iCloud and "Find My" is on then the location of your device is shown on a map when you log in to your account on a browser and/or another device. Useful if you misplace your AirPods case or your other devices including the one with the Apple Tags.
Passwords and Passkeys.
Here is where it gets interesting. Imagine a future without passwords. Passwords can be eventually guessed or can be obtained with some social engineering skills. If you don't mind some technical language I found this WWDC video quite enlightening: Deploy passkeys at work, which is the continuation of last year's Meet passkeys.
Also, it is explained in plain English here: passkeys.
Safari Fraudulent Website Warning and End-to-End Encryption
Quite self-explanatory. Safari and mail automatically warn you of suspected phishing websites and encrypts your sent messages.
Notify When Left Behind.
I get notified when my devices are taken away or misplaced, like my AirPods case. I am quite paranoid about it and this gives me some piece of mind. Also, when I leave home in the morning my iPhone sends me a reminder when I forget my airPods behind. This is very helpful because I really need them. They have become indispensable to my workflow and to listen to music when I write a post :)
MDM Remote Lock.
Locks devices remotely. No one can get in until they enter a PIN. MDM is for Mobile Device Management. It is used in companies to track employees' devices. As a normal user, you will not have access to this feature. Also, it works only with an MDM server.
MDM Remote Wipe.
Same as above. It is a feature enabled by the MDM server. Remotely wipes all personal and proprietary data on a lost device.
Secure Enclave.
As the name suggests, it is an on-device encryption enclave. An extra layer of security on your device keeps everything encrypted. If you have read the last Cory Doctorow book, Red Team Blues you might remember about the story of this group of people trying to force the Secure Enclave of the iPhones and get access to billion of devices. It is fiction of course!
I am talking more about the Secure Enclave below.
Family Sharing.
As the video shows, it keep track of your favorite people. If their device goes missing, you can help find it. I am not sure it will work the other way around in my case, but it is a security feature nonetheless! 😇
In the early days
The above is fun, but it is not the whole picture.
I have been a Mac user since the 90s and I never had any other computer. Ever since the early Mac OSX times, I never thought about security on a Mac.
Mac users like me thought of Macs as simply safe right out of the box and that Macs don’t get PC viruses"...
Over the years, the Mac userbase has grown substantially, and with that, so has its attractiveness to potential attackers. No longer is it the niche underdog; instead, it has become a lucrative target due to its expanding popularity.
In 2005, with the release of OS X Tiger Apple started to request the user password for new downloads and installs. Since then the Macintosh share between laptops sold worldwide has risen tremendously year by year.
From an Interview with Steve Jobs in 2005 at All Things Digital:
“Avie Tevanian, the person that was running software at the time, showed us OS X and every time you wanted to load an application into OS X, whether it was off the internet or even off a disc, you had to type your name and password–you had to authenticate. And we gave him incredible shit for that. We said ‘Avie, are you nuts? This is the Mac!’ And he said, ‘Trust me.’ And so we deferred to Avie on that after trying to twist his arm for a year. And boy, was he ahead of his time.”
Some Apple security history
OS X Leopard (10.5) introduces File Quarantine.
OS X Snow Leopard (10.6) introduces XProtect which compares downloaded files against a database of known malware, and significantly improved File Quarantine.
Mountain Lion OS X (10.8) in 2012 introduces Gatekeeper. Code signatures and a first version of what will become Gatekeeper software were introduced already around 2007.
macOS Catalina (10.15) introduces application notarization as a requirement for Mac Apps. There is a great talk about this at WWDC19 All About Notarization
macOS Monterey (12.3), 14 March 2022, added XProtect.app in the CoreServices folder in the system library.
Mac Security today
Apple Silicon Macs are considered more secure due to a combination of hardware and software features designed by Apple.
Custom-designed hardware: Apple Silicon Macs are powered by Apple's custom-designed ARM-based processors. These processors are built with a focus on security, including features like hardware-based encryption and secure enclaves.
Unified memory architecture: Apple Silicon Macs use a unified memory architecture, which means that the CPU, GPU, and other components share the same memory pool. This design reduces the attack surface and makes it more challenging for malware to exploit certain memory-related vulnerabilities.
Secure Enclave: Apple Silicon Macs include a dedicated hardware security component called the Secure Enclave. The Secure Enclave is responsible for handling sensitive data like biometric information (e.g., Touch ID and Face ID) and cryptographic operations. It operates independently of the main processor and operating system, making it more difficult for unauthorized access to this sensitive information.
Enhanced security features: Apple continually introduces new security features in its macOS updates. For instance, technologies like "System Integrity Protection" (SIP) and "Gatekeeper" prevent unauthorized modifications to system files and restrict app installations to those from the App Store or identified developers, respectively. This helps protect against various types of malware and unauthorized software.
App sandboxing: Apps on macOS are sandboxed, meaning they are restricted in accessing files, data, and other system resources. This containment reduces the potential damage that malicious apps can inflict on the system.
Notarization: which is about identifying and blocking malicious Mac software prior to distribution, without requiring App Review or the Mac App Store, and widely adopted by Mac app developers.
Tools
Correct me if I am wrong, but I do not believe in third-party security tools for Mac running in the background like in Windows PCs.
However, one utility that caught my attention is SilentKnight by the Eclectic Light Company. SilentKnight by the Eclectic Light Company.
This free utility helped me stay informed about the latest Mac security updates and provided some insights into how my Mac defends itself against emerging threats.
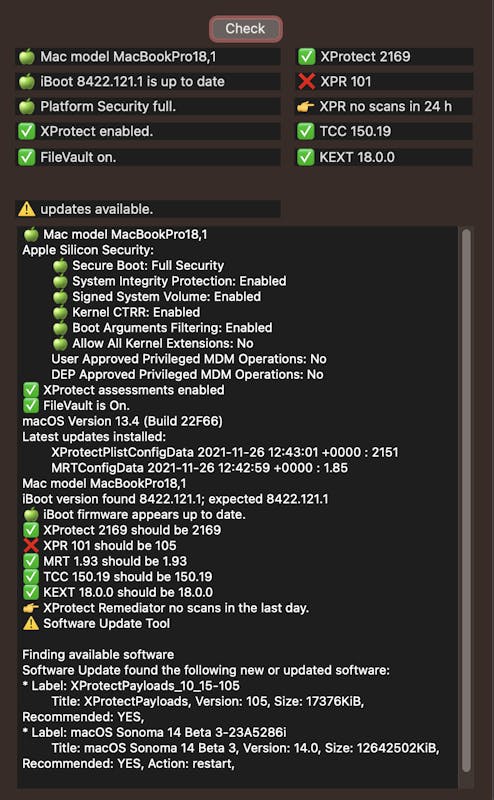
What I like here is that the app allows you to download "named updates".
For instance, at the bottom of the previous screenshot, there is a message saying that there is new updated software which doesn't show in my system settings. I can download it separately by copying and pasting the name into a new window:
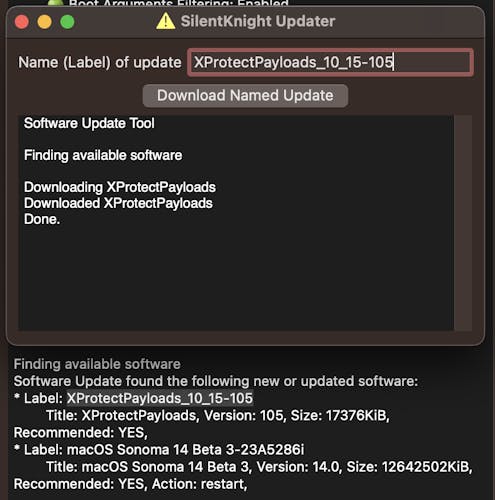
and once downloaded it opens them in the finder for me to action
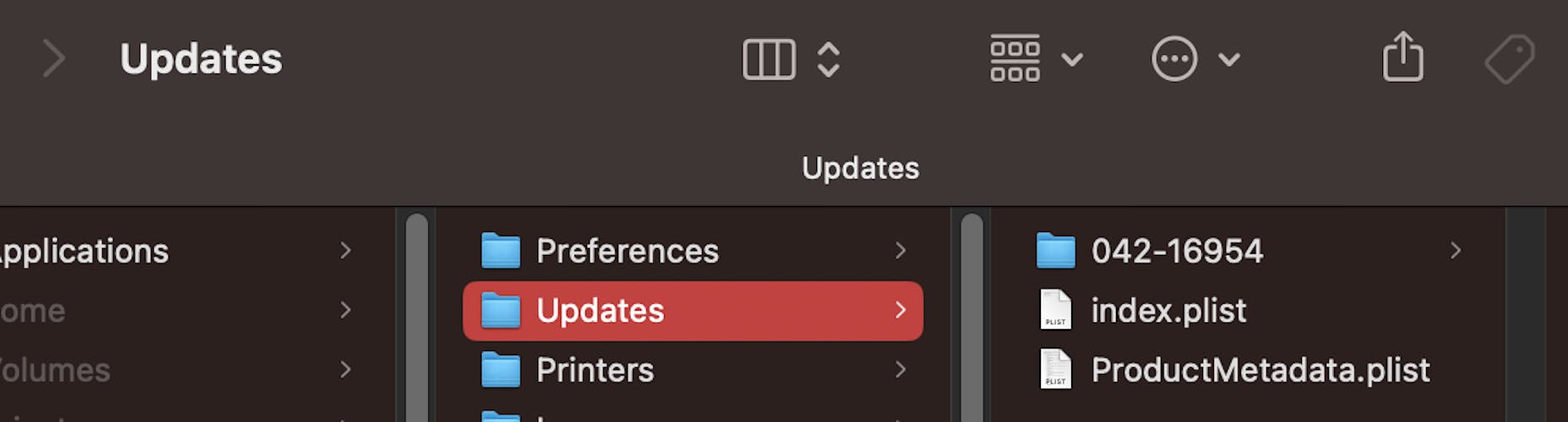
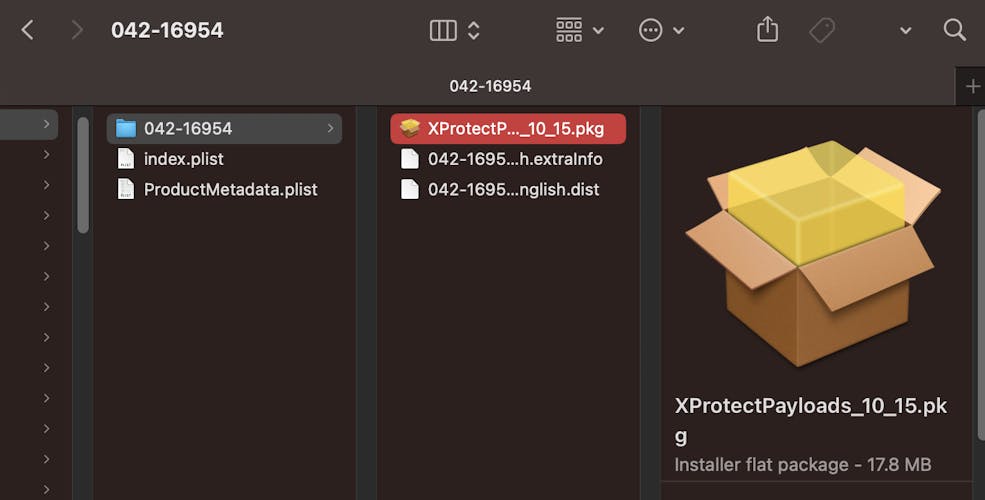
So I install the patch which probably would have been included in the next security update anyway, but it is nice to be somewhat ahead!
Some more explanation of the security keywords used above
iBoot shows the currently installed firmware. In Intel Macs without a T2 chip, it would show the EFI firmware, for Apple silicon Macs it is the iBoot version
FileVault encodes the data on your startup disk so that unauthorised users can’t access your information. Apple
System Integrity Protection (SIP) protects the system files from modifications.
Signed/Sealed System Volume. In Big Sur and later the data and system are on different partitions and sealed.
XProtect and XProtect Remediator are malware scanners. They check the file signatures against a list of known malware and if something is found the Remediator will disable the execution of the file.
MRT is a now somewhat older anti-malware tool.
TCC is Transparency Consent and Control.
The KEXT version is a list of extensions to load.
Gatekeeper among others keeps track of revoked app certificates but it is now somewhat older and less frequently updated.
To recap
This made me realise that, despite its reputation for being secure, a Mac still requires proactive measures to maintain its safety.
In today's fast-paced, interconnected world, safeguarding our digital data has become paramount. Mac users, in particular, have long appreciated the security benefits of Apple's ecosystem. However, as cyber threats continue to evolve, it's crucial to stay vigilant and enhance our Mac security measures.
I think Mac security is a very interesting subject and there is a lot to learn. Apple is understandably is very secretive about these tools, but it is nice to know that they are there and that Apple silicon Macs have even extensive additional security baked in.
Links
Steve Jobs in 2005 at All Things Digital.
The Eclectic Light Company: A Short History of Malware Protection in macOS.
About The new Protect App in Monterey
The free SilentKnight utility: SilentKnight.
What does SilentKnight check and why?.
https://support.apple.com/en-gb/guide/security/sec469d47bd8.
https://eclecticlight.co/2023/07/12/how-to-check-your-mac-is-secure/.
